Students
Home » Students
Cybersecurity is a rapidly growing industry that faces a severe talent shortfall
3.5 million unfilled jobs globally by 2021. As of 2020, approximately 50% of surveyed firms plan to increase their cybersecurity staffing1
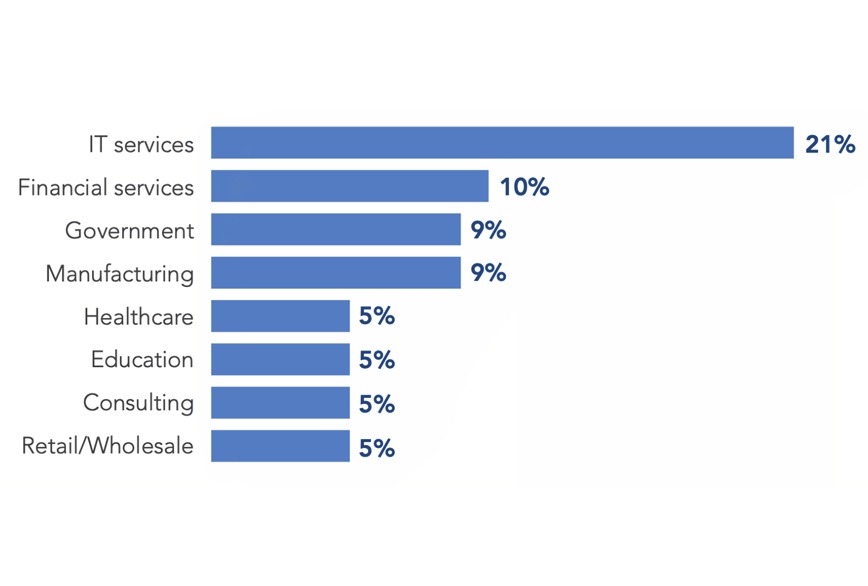
Approximately 60% of employers say they are unable to recruit personnel with desired skillset and, because of staff shortages, face significant security risks
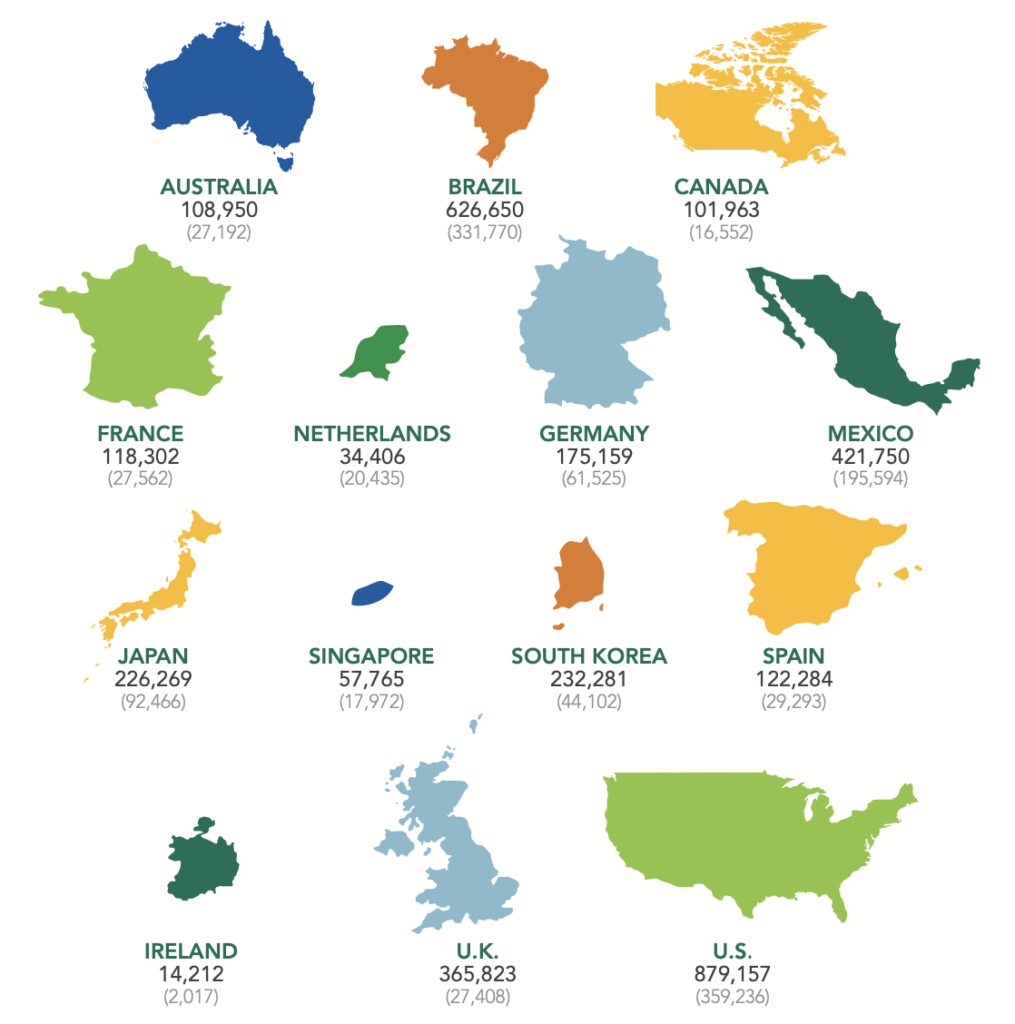
Less than 10% of millennials expressed interest in a career of cybersecurity because of lack of familiarity with the industry. Yet for every 100,000 businesses, there is estimated to be 10,300 cybersecurity professionals. In the US, for every 1 million U.S. workers, there are approximately 4,600 cybersecurity professionals2
Cybersecurity professionals develop a rewarding career with stimulating opportunities to tackle challenging problems
Cybersecurity professionals protect businesses of all sizes across the globe. Job satisfaction among cybersecurity professionals is remarkably high (over 75% are satisfied) and has been growing
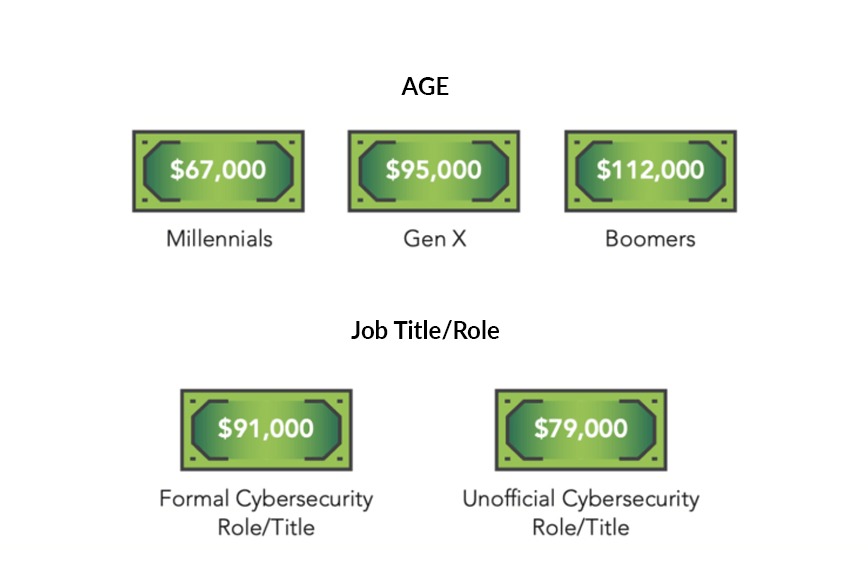
On average, cybersecurity professionals make ~$83,000 per year in base salary, with those who have greater experience earning as high as $112,000
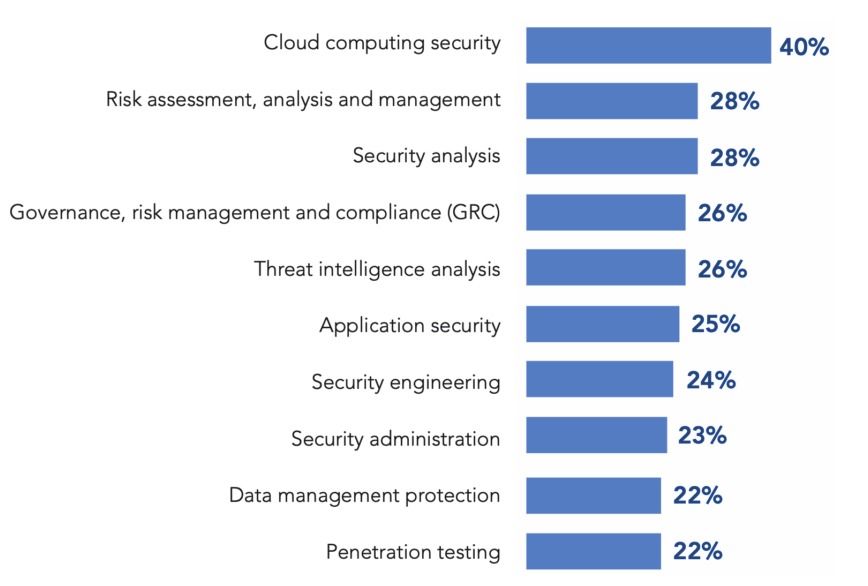
By building a career in cybersecurity, professionals learn top skills needed to operate invaluable processes, conduct information analysis, and provide threat protection
Apply Now
Application Qualifications
- Student: If you are currently an enrolled student or have graduated from an accredited academic institution. All majors are accepted.
- Professional: all professional working backgrounds are welcome, including those from traditional (IT, computer science) and non-traditional backgrounds
- We especially want to encourage you to apply if you belong to the following groups:
- Women
- African American
- LatinX
- American Indian or Alaskan Native
- Native Hawaiian or Other Pacific Islander
Program Commitment
- Complete online technical training coursework to enhance your technical skills and knowledge. Participate in lab training for hands on research
- Expect active participation and do not be absent for more than 2 classes. Given COVID, for the time being all classes will be held virtually
- Maintaining contact with your NextGen mentor, an excellent resource to help you with any advice on how to navigate skill development, corporate culture, and recruiting process
- Be prepared to learn and be hungry. We are looking for those who are passionate about learning new technology, committed to problem solving, and dedicated to managing risks
- Upon successful completion of program and placement into a job, to be available to serve as volunteer coaches or NextGen representatives for future classes
Cohort Details
- Q1 2021
Full time - Application deadline
Jan 11th, 2021 - Dates
Jan 18th – Feb 12th, 2021 - Schedule
M – F: 9 am – 3 pm PT - Format
Virtual/Online
Apply Now
Application Qualifications
- Student: If you are currently an enrolled student or have graduated from an accredited academic institution. All majors are accepted.
- Professional: all professional working backgrounds are welcome, including those from traditional (IT, computer science) and non-traditional backgrounds
- We especially want to encourage you to apply if you belong to the following groups:
- Women
- African American
- LatinX
- American Indian or Alaskan Native
- Native Hawaiian or Other Pacific Islander
Program Commitment
- Complete online technical training coursework to enhance your technical skills and knowledge. Participate in lab training for hands on research
- Expect active participation and do not be absent for more than 2 classes. Given COVID, for the time being all classes will be held virtually
- Maintaining contact with your NextGen mentor, an excellent resource to help you with any advice on how to navigate skill development, corporate culture, and recruiting process
- Be prepared to learn and be hungry. We are looking for those who are passionate about learning new technology, committed to problem solving, and dedicated to managing risks
- Upon successful completion of program and placement into a job, to be available to serve as volunteer coaches or NextGen representatives for future classes
Cohort Details
Technology Resilience Training
Part Time:
Jun 1st, 2024 - Jun 30th, 2024 (Virtual Online)
Technology Resilience refers to the ability of company to withstand and recover from unexpected technology disruptions, failures, or attacks while maintaining essential business functions. In today’s interconnected and technology-dependent world, Technology Resilience has become an increasingly important topic.
This course is designed to explore Technology Resilience and its related concepts in detail. After introducing the student to the basics of Technology Resilience, it details how organizations can determine their most critical technology requirements. Following this, it details how organizations create Technology Resilience strategies and plans to protect critical technologies in case of a disruption. Lastly, it discusses how organizations conduct exercises to familiarize recovery teams with their plans.
Students will be guided through a series of interactive virtual presentations, where they will be met with knowledge checks along the way. As they progress through each module, the students will gain a deeper understanding of technology resilience and its requirements, governance, strategies, plans, and exercising. At the end of the training, students will walk through a case study and take a final exam to test their knowledge of the subject matter.
Schedule:
A 3-part self-paced training, with progressive and interactive training modules:
Part 1:
• Module 1: Introduction to Resilience and Technology Concepts - This module introduces Technology Resilience and current Technology Resilience trends. Additionally, it provides students with an overview of the Technology Resilience Framework alongside common definitions and related topics.
• Module 2: Technology Resilience Governance: This module explores the role of governance within Technology Resilience. After outlining the activities required to develop Technology Resilience governance, it covers Technology Resilience policy and reporting.
• Module 3: Requirements Analysis (BIA & TIA): This module focuses on how organizations conduct a thorough analysis of their critical business processes, systems, and technologies. After introducing the students to Business Impact Analysis (BIA), this module provides a detailed explanation of the Technology Impact Analysis (TIA) process, which is used to inform the development of Technology Resilience strategies and plans.
Part 2:
• Module 4: Technology Resilience Strategies: This module delves into the strategies and methodologies for designing resilient technology systems and infrastructure. From on-premise and cloud strategies to hybrid strategies that mix the two, this module explains the ways organizations can implement resilience strategies to mitigate potential disruptions.
• Module 5: Technology Resilience Plans: This module covers Technology Resilience plans, which serve as a crucial reference when building a resilient technology infrastructure. After introducing the concept of resilience plans, students will learn about the three main types of Technology Resilience Plans: Infrastructure Recovery Plans, Application Recovery Plans, and Orchestration Plans.
• Module 6: Technology Resilience Testing/Exercising: This module emphasizes the importance of regularly exercising and validating Technology Resilience plans. From tabletop to full exercises, students will learn how each type of exercise plays a critical role in ensuring continued Technology Resilience.
Part 3: Summary and Practice Case Study
• Module 7: Summary & Key Takeaways: To conclude and prepare students for the case study/exam, this module provides an overview of the key topics and takeaways from the previous 6 modules.
• Module 8: Case Study: This module contains a practice business case, applying the content covered in the previous modules to a real-world scenario. Students will be required to use the knowledge gained throughout the course to answer a series of questions based on the information provided in the case.
After reviewing the course material and applying it to the case study, students will test their knowledge of Technology Resilience with the following:
• Final Exam: A 30 multiple-choice question final exam concludes this training.
Student Referral
We would love it if you told your friends and colleagues about NextGen programs. We respond to all inquiries within 48 hours. Please provide us with your details so we can get in touch.
Support Center
Our friendly and knowledgeable support staff is ready to help you with registration, training, placement, and anything you need assistance with. We respond to all inquiries within 48 hours.

A non-profit providing a platform to increase diversity and inclusion in the cybersecurity industry. It brings together cybersecurity experts, solution providers and enterprises to make a difference in this community and address a mounting cyber skills shortage and talent gap.
-
NextGen Cyber Talent Inc.
999 West Taylor Street,
Suite A
San Jose, CA 95126 - contactus@nextgencybertalent.com